
Jerry Wiggins
Last updated:Sep 21, 2023
Google’s best free email service is Gmail. A large portion of the global population uses Gmail accounts for email services, and accessing services that call for a Google account always requires having the @gmail.com extension. The majority of users use their Google Gmail accounts to secure their devices, leaving them open to hackers. Hackers may attempt to gain access to the data on your device by hacking your Gmail account if you use it as your primary backup account.This post examines and walks you through the reasons why Gmail accounts get hacked, as well as how to hack a Gmail account, check whether your account has been hacked, stop your account from being hijacked, and restore a hacked account.

Part 1. Why Hack Gmail Accounts
Identity theft is accomplished via hacking Gmail accounts. Your Gmail account can be hacked in order to evaluate the security of the Google Account service. If your emails contain information that hackers find interesting, they can use a Gmail password hack to reset your account and read your emails. Key interest agents, government employees, and professionals are among the groups most vulnerable to this type of hacking. The information they communicate in emails through Gmail accounts is vulnerable to attack by rivals or political adversaries. Because they like the rush of taking over an account, some hackers are skilled at hacking Gmail accounts.
Part 2. How to Hack Gmail
Hacking software, phishing and social engineering assaults, password managers in your browser, surveillance apps, and insecure password resets are all ways that someone can gain unauthorised access to your Google account.
1. Using Spy App Without Password
Using a spy programme, you can successfully hack a Gmail account without a password, regardless of your level of experience or lack thereof. The most effective spy software for Gmail account hacking is called Digitexpro. Digitexpro is not limited to hacking Gmail accounts; it can access any data on a device. For installation, the app needs one-time access to the target user’s device.You won’t need to use the device for hacking or spying after that.Since the app is invisible, the target device cannot detect it.It records and sends reports to your remote control panel while running in the background.You can use your remote control panel to send or delete emails on the target device without anyone noticing.
Visit digitexpro.net and select the “Try Now” option to download Digitexpro. Register and create an account. After selecting a plan, you will get an email with installation instructions. On the target’s device, install the Digitexpro app and follow the setup instructions. To remotely execute any operation on your target’s Gmail account, log into your mSpy control panel account. The keylogger, screenshot, and monitoring features of mSpy are essential for breaking into a Gmail account.
Monitoring Feature
You may keep an eye on a target’s phone usage, including all sent and received emails, by using Digitexpro. Log into your remote control panel after installing mSpy on the target’s device to keep an eye on their emails without having to physically access it.
Screenshot Feature
Every five minutes, Digitexpro sends you an update via your control panel dashboard with a report of the captured data, along with images of phone activity. Viewing all email activity, calls, messages, browsing history, location, social networking messaging, and multimedia files are all included in the recorded data.
Keylogger feature
On a target device, the Digitexpro keylogger capability logs each and every keyboard tab. The app can convert the recorded keystrokes into a password when a user enters their password to access their Gmail account.
2. Using Browser Password Manager
When you auto-save your passwords, the browser manager keeps track of them all. When you physically gain access to a target person’s device, you can access their passwords. Click the three dots in the upper right corner of the target’s device browser. Go to settings, select the passwords tab, and scroll to see every password that has been automatically saved. The password for the account you have selected will appear once you click on it. To view the password if it is not locked, click the eye icon.
3. Using The Password Reset Method
If the target hasn’t configured the recovery to confirm the method, the password method can modify their password. You can reset their password by acquiring the reset confirmation code if they have specified a text message or another email as their recovery method and you are in contact with them. To keep them from learning about the reset, delete the confirmation code.
4. Using Hacking Software And Serial Keys Generator
To hack Gmail IDs, one can download hacking software, which has an easy-to-use interface. To get the target person’s password, download the hacking software and follow the on-screen instructions. Both iOS and Android smartphones can download these apps. Visit the website and enter the target user’s Gmail account to use the serial keys generator to hack a Gmail account password. Click “I agree” to proceed. The web service will quickly show the password after executing a Gmail password hack.
5. Through Professional Hackers
Expert hackers are aware of the technological pitfalls and shortcuts involved in gaining an unauthorised Gmail password. You can pay a skilled hacker to get your desired password, saving you the trouble.
6. Using Phishing And Social Engineering Attacks
Phishing is a technological hacking technique that involves forging an email account and using a landing page link to fool the target into entering their password in order to obtain the desired data. The intended recipient receives the link and is prompted to enter their password. The information of the target individual is then instantly intercepted by the hacker. The target of a successful phishing attempt may get a notification that their account has been compromised.
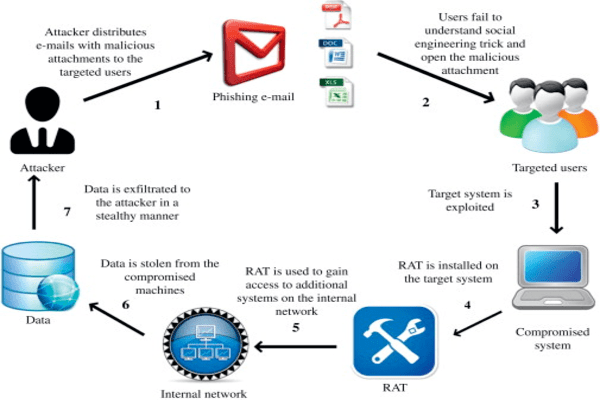
Part 3. How To Check If Your Gmail Account Has Been Hacked
The following are methods to check if you have been hacked.
1. The Have I Been Pwned site
You may determine whether your Gmail account has been compromised by visiting the have I been Pwned website. Go to the Have I Been Pwned page to perform the check. To find out if your Google account has been compromised, sign in with your Gmail credentials and click the “pwned?” symbol.

2. Check for suspicious account activity
If you notice suspicious activities, such as new and unusual apps or websites on your phone or browser, your google account has been hacked. Reset your Gmail account password to secure your account.
Part 4. How To Prevent a Gmail Account From Being Hacked
1. Don’t click on any suspicious link
Links that raise suspicions are designed to lead you into a phishing scam. Never click on any dubious links; instead, delete them.
2. Use Antivirus Software
Malware and unauthorised parties are prevented from accessing your data by antivirus software.
3. Don’t Share Your Device
Sharing your smartphone provides hackers the advantage to access your data, including passwords, or to covertly install spy and hacking software on it to violate your privacy.
4. Choose a Strong Password
By making your password difficult to guess, using a strong password deters hackers.
5. Don’t Share Confidential Information
By disclosing private information, hackers can reset your passwords and carry out password hacks via third-party access.
6. Turn on two-factor verification.
You’re prompted to input a code supplied to you using the recovery method you’ve chosen after entering your password.
Part 5. How To Recover a Hacked Gmail Account
1. Use The Recovery Email or Phone Number
Click on the “Forgot Password” message if your Gmail account has a recovery email address or phone number stored in it.
2. Use The Recovery Page of Google
To recover a hacked Google account:
1. Visit the google recovery page and select the account recovery option.
2. Answer all the questions required to confirm your identity on your google account.
3. Set a new password and secure your account.
3. Create a New Gmail Account
You can safeguard all of your accounts with a new account and remove the compromised one from them.
